There is an increasing number of business applications on corporate mobile phones these days. There are threats to consider and risks involved when releasing corporate financial or other types of sensitive information on the go. Enterprises are responsible for mobile application and device security in their day-to-day business. In case of a loss of sensitive organizational data, management is held accountable. This article explores the risks surrounding the use of mobile business applications by employees and the measures organizations can take in order to become and stay in control.
Introduction
Organizations across the globe are developing or using mobile applications in order to increase employee productivity. Mobile technology fulfils an increasingly important role within business processes. Users have been familiar with mobile access and apps for a while to retrieve real-time information anywhere at any time. It is therefore no surprise that more organizations are providing access to financial and customer information via mobile devices.
As a relatively new way of working, this may pose additional challenges (e.g. lost/stolen mobile devices, mobile security) and consequently, result in security risks. In addition, already existing challenges such as malware, employee security awareness are also still applicable and cannot be neglected. Therefore, a strong focus on mobile application security and the accountability of management for the underlying risks is required. When identified risks are not addressed sufficiently through detailed risk assessments and implementation of a coherent set of security measures, sensitive financial data may become compromised. Using mobile applications in organizations raises the question whether additional measures – in comparison to regular online business applications – are needed to cover the security risks related to mobile business applications.
Recognizing these risks, organizations will become more aware of their responsibility for mobile application and device security. A risk/control framework will help organizations to guide their approach to control all risks involved and to be able to continuously test and update the security posture. This article focuses on securing mobile business solutions by determining which risks exist and how these could be controlled.
Relevance of securing mobile business applications
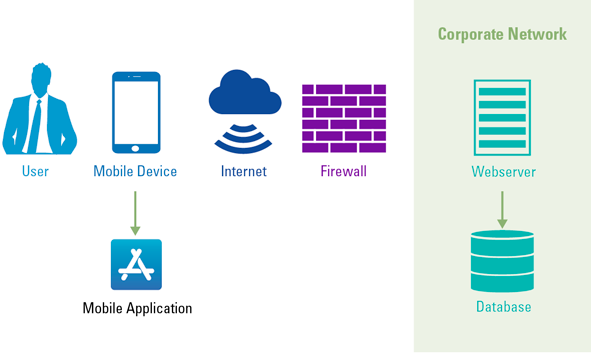
Mobile devices have evolved from merely providing access to enterprise e-mail to removing logistical process delays and tracking business transactions at any time through the use of mobile business applications. For example, these applications provide the organization the ability to review, approve or reject purchase requisitions and supplier invoices, continuously follow their order backlog and keep track of their Order-to-Cash and Purchase-to-Pay process performance trends in real-time. Mobile applications are rapidly becoming the primary – and maybe even single – communication channel for customers and employees and therefore the applications are expected to be secure and to protect privacy ([Ham17]). Despite numerous positive and useful features/benefits, the use of mobile applications in organizations also poses certain threats. In the context of this article, we ought to identify the (f)actors involved when using mobile business applications to identify potential threats. The actors identified are shown in Figure 1: the user, the mobile device, mobile application, the internet, firewall, the corporate network, webserver, and database.
Figure 1. Actors mobile business applications in a highly simplified figure. [Click on the image for a larger image]
The main threats taking the involved actors into account are discussed next.
Unprotected applications or networks
When network gateways are placed at easily accessible locations and include unpatched vulnerabilities, it may enable hackers to control the network gateways and intercept communications ([Enis17]). If so, it could lead to severe data privacy violations associated with the applicable GDPR legislation. Incidents may occur where sensitive organizational data is lost, which would have a significant negative impact on an organization’s reputation leading to financial damage. The implementation of the bring your own device (BYOD) policy at organizations acts as a complicating factor, as personal devices have diverse interfering applications installed.
Mobile security unawareness
Employees are considered to be the weakest link in information security ([Line07]). When there is limited awareness among employees regarding the security of mobile devices and the classification of data that is stored on devised and in the applications, this could bring about security incidents. For example, when sensitive organizational data is sent to personal non-managed devices by employees trying to meet a deadline. Most employees view security as a hindrance to their productivity. In case a way is found to work around security measures, there is a high chance that it will be used.
(Un)intended employee behavior
Employee behavior can have a substantial detrimental impact on the security of mobile business applications. When employees are insufficiently aware of the risks involved, their mobile activities could undermine the technical controls that organizations have in place to protect their data, such as incidents to consider, cases of malicious employees that have terminated, but that still have access to corporate applications on their mobile devices or cases where the mobile device is lost or stolen, etc. ([ISAC10]).
Access by external parties
External parties who have access to the network and systems of the organization are difficult to manage and monitor. Third parties are a known source of significant security breaches and are a target for hackers (as a steppingstone). This introduces more vulnerabilities and an increased risk to the corporate environment. These external parties usually require high privileged access to infrastructure and systems and therefore impose a high impact if those privileges are misused or compromised.
The growing use of mobile devices within organizations has increased the threat level of IT security breaches, misuse of sensitive data and – as a result – reputational damage. Therefore, it is imperative that mobile business applications are subject to periodic audits performed by IT auditors.
In order to effectively perform such an IT audit, it is important to start with a risk assessment and to leverage a control framework designated for mobile business applications. To perform an IT audit effectively, the scope should only include the most relevant actors where organizations are able to influence and mitigate the risks involved. This leads to the following audit objects which are in scope for the designed risk/control framework:
- User
- Mobile device
- Mobile (business) application
- Corporate network
Considering the objects in scope and the threats identified in the previous section, a risk assessment is performed in which risks are evaluated which are deemed relevant to the subject of mobile business applications. These risks should be controlled by organizations when using mobile business applications as part of their operational processes and will serve as a basis for identifying related mitigating controls. The audit objects, the risks and the controls are combined in a risk/control framework which is included in this article.
Risk/control framework mobile business applications
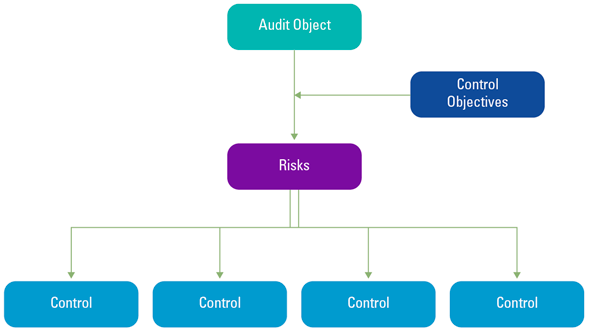
The risk/control framework has been established by analyzing theory, identifying relevant objects and performing a risk assessment. The interlinkage of the appropriate controls, the risks, the control objectives and the relevant audit objects is depicted in Figure 2. The control objectives are desired conditions for an audit object which, if achieved, minimize the potential that the identified risk will occur. Hence, the control objectives are linked to the identified audit objects and are subject to the risks that threaten the effectiveness of the control objectives. The controls should mitigate the security risks to which mobile business applications are exposed.
Figure 2. Establishing the risk/control framework. [Click on the image for a larger image]
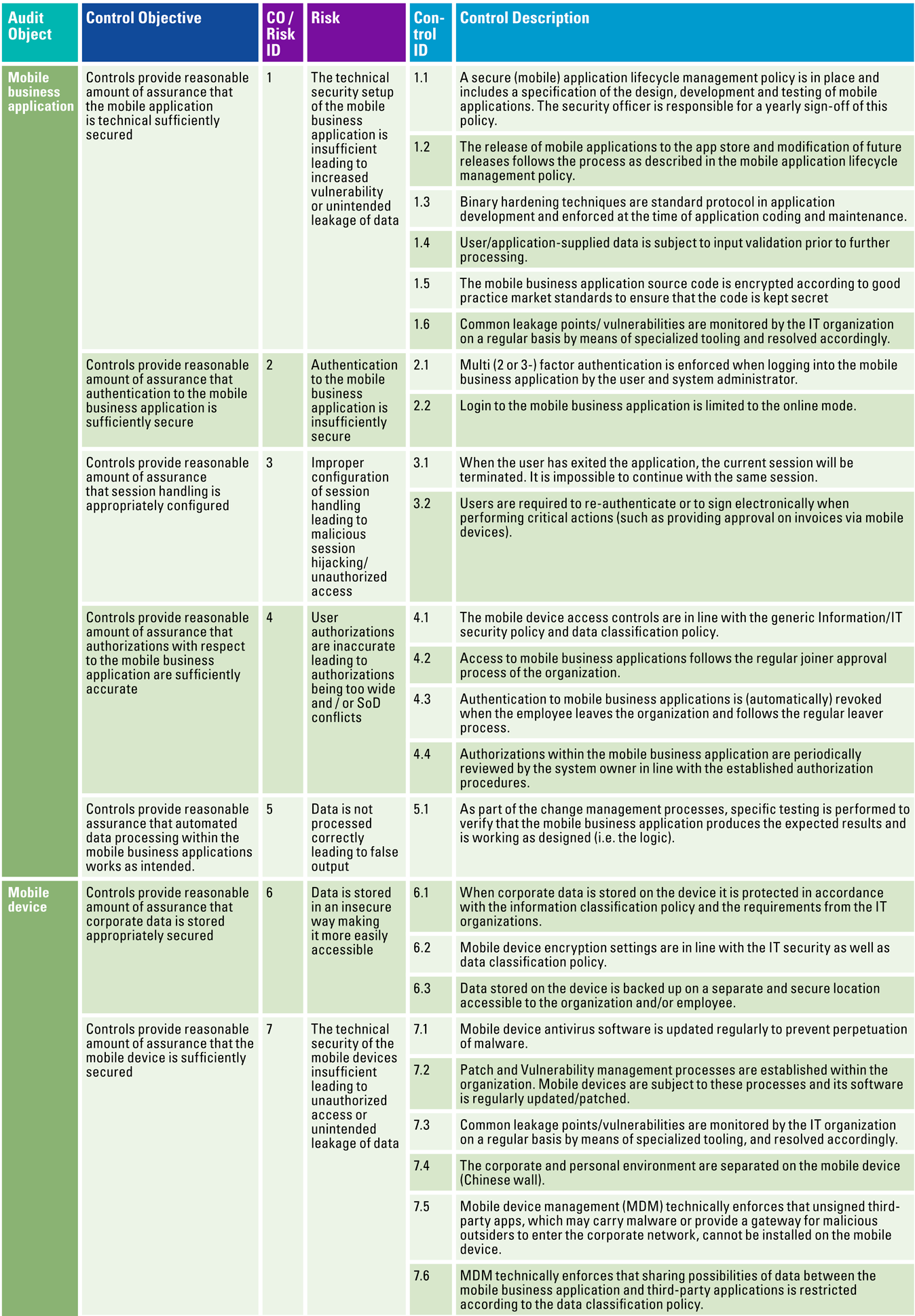
Resulting from the aforementioned described process of setting up a risk/control framework, Table 1 shows the risk/control framework that has been established.
Table 1. Risk/control framework mobile business applications. [Click on the image for a larger image]
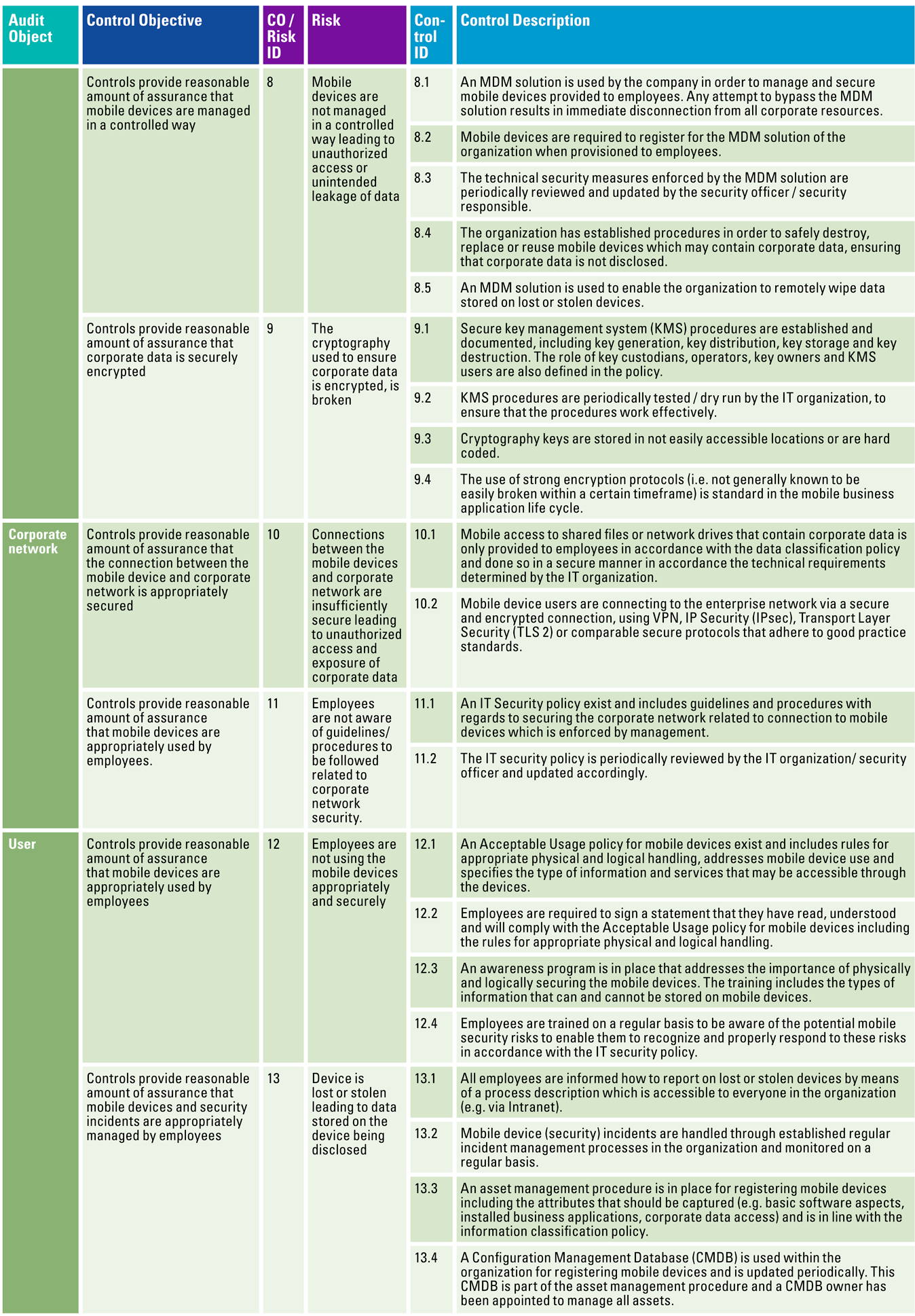
Table 1 (continued). [Click on the image for a larger image]
Control objectives of the risk/control framework explained
The risk/control framework can be used by organizations in order to continuously test and update technical measures related to the usage of mobile business applications in order to safeguard the organization and its sensitive data.
Controls related to the technical setup of the mobile business application and a secure application life cycle management, control objective 1, are vital and need to be taken into account. These controls focus on tracking the risk of an application as it moves through the development lifecycle. Binary hardening, input validation and encryption complement a secure development environment to prevent vulnerabilities and unintended leakage of data from unprotected applications. These controls are even more relevant for mobile business applications as mobile devices are taken everywhere and most likely contain sensitive business data.
Securing the mobile business application by means of sufficient authentication and authorization configuration, control objective 2, 3 and 4, is relevant for the mobile business applications, but is highly dependent on how the IT infrastructure and the mobile environment has been set up. Even though it could be that part of the authentication logic is performed by the back-end server, it is important to consider this as integral part of the mobile architecture. Plainly, authentication and authorization problems are prevalent security vulnerabilities and rank second highest in the OWASP Top 10 ([OWAS17]) and are therefore included in the established risk/control framework.
In order to prevent unauthorized access and unintended leakage of corporate data, it is also vital to incorporate the right technical security measures to protect the mobile device (e.g. anti-virus, patch and vulnerabilities, separate corporate and private environment and data sharing). The controls, control objectives 6, 7 and 10, that are related to these technical measure are a very important part of the risk/control framework: it would trigger organizations to rethink their mobile architecture strategy, to be continuously aware of potential vulnerabilities and to implement and monitor the security measures.
In order to steer organizations in their strategy to control their mobile environment, controls related to MDM solutions are also incorporated. An MDM solution, control objective 8, will provide input to secure, manage and monitor corporate owned devices that access sensitive corporate data.
Cryptographic controls on mobile devices are almost inevitable. As mobile devices may contain sensitive corporate data, a secure manner of protecting data using cryptographic techniques is required; control objective 9. Cryptographic controls will provide added value to organizations for protecting their mobile data.
Mobile devices should be safeguarded from external threats. Therefore, when connecting to the corporate network, stringent security standards should be applied to protect corporate data; control objective 5 and 11. Controls related to these security standards will guide the organization in how to continuously monitor and test connectivity security between mobile devices and the corporate network.
A well-known saying in the world of IT security is that people are the weakest link in cyber security. We would like to reframe that as: people are the most important link in the cyber security chain. The risk/control framework incorporates “soft controls” – control objective 12 and 13 – related to users (people aspect) of mobile devices.
In conclusion, the risk/control framework consists of several sections that relate to:
- secure development
- technical setup
- authentication & authorizations
- cryptography
- sessions handling
- using MDM
- data security
- connections with corporate network
- user awareness and
- device / asset management.
Relevance of implementing a mobile security risk/control framework
In today’s world full of IT business transformations, it is important to implement controls for securing corporate data on mobile devices. Mobile business applications will continue to gather momentum in the coming years – despite the fact that the technical security level achieved will remain a concern. The risk/control framework as developed can be used in practice as a reference framework. As the mobile environment is rapidly evolving, there is a need to continuously test the security level and control the risks identified. Although there is an abundance of literature detailing specific technical security measures to be configured or implemented, these measures are usually not incorporated in (existing) risk/control frameworks. This framework is keeping abreast of new technology trends.
The aim of this article is to trigger organizations to think about these controls and how they can adjust this framework to make it applicable to their IT (mobile) environment and to incorporate these controls in their existing control framework that are most likely focused on regular ERP systems or IT General Controls. Since businesses and IT information chains have grown more sophisticated and complex, mobile applications become more prevalent at numerous large organizations.
Looking forward
As the Dutch National Cyber Security Centre ([NCSC18]) states in their mobile applications research; organizations are using these applications more and more in their daily business activities. The differences between the backend of mobile phones, tablets, laptops and desktops are diminishing, however. In the near future, the IT auditor needs to focus on end-to-end device and mobile security, which is not yet fully integrated in risk/control or audit frameworks or taught at post-master IT auditing studies.
Conclusion
This article is aimed at showing the need for and providing a risk/control framework. The risk/control framework we developed and validated can be used by organizations to continuously test and update technical measures in and around mobile business applications. This will safeguard their organization and its sensitive data. There is a number of significant controls an organization should have in place in order to securely use mobile business applications. This article demonstrates that several mobile application areas need to be addressed using security controls. These areas are secure development, technical setup, authentication & authorizations, cryptography, sessions handling, using MDM, data security, corporate network connectivity, user awareness and device / asset management. We do emphasize that how organizations control their mobile environment is also dependent on several factors. It is critical to perform an extensive risk assessment that addresses the business as well as technical aspects to identify the IT maturity of the organization, risk appetite and how the mobile infrastructure has been designed and configured. The risk/control framework can be adjusted according to this assessment, by verifying the controls that are applicable to the organization.
References
[Enis17] Enisa (2017). Privacy and data protection in mobile applications. Retrieved on June 22, 2018, from: https://www.enisa.europa.eu/publications/privacy-and-data-protection-in-mobile-applications
[Ham17] Ham, D. van, Iterson, P. van & Galen, R. van (2017). Mobile Landscape Security, Addressing security and privacy challenges in your mobile landscape. KPMG.
[ISAC10] ISACA (2010). Securing Mobile Devices.
[Line07] Lineberry, S. (2007). The Human Element: The Weakest Link in Information Security. Journal of Accountancy, 24(5), 44-46, 49.
[NCSC18] National Cyber Security Center (NCSC-NL) (2018). IT Security Guidelines for Mobile Apps. Den Haag.
[OWAS17] OWASP (2017). OWASP Top Ten. Retrieved on June 2018, from: https://owasp.org/www-project-top-ten/