This article describes the main outcomes of a CA/CM survey, a CA/CM success story and important lessons learned for a CA/CM implementation. The survey was conducted within the EMA region (Europe, Middle East, and Africa) and was intended to determine the current status and future expectations of CA/CM within organizations. The main conclusion was that, although organizations understand the benefits of CA/CM, current adoption of CA/CM is still low due to hesitation. Based on the survey results we concluded that the problem was not any negative attitude toward CA/CM; rather, the low adoption was mainly caused by not knowing how to apply CA/CM to the organization and how to determine the business case for it. We have included a CA/CM success story where, based on events, the need and business case for CA/CM were evident. This organization implemented CA/CM throughout the whole organization to prevent fraud and also found other cases for using CA/CM. The final part of this article describes important lessons learned for successful CA/CM implementations to help other organizations achieve their own CA/CM success stories.
Introduction
Organizations are nowadays faced with increasing pressure, both internal and external, to provide assurance on financial reporting and on the reliability and effectiveness of their business processes. For example, we will describe a case where the client paid a fine of 150 million euros for failing to follow government regulations. At the same time, organizations want to have more insight into how risks are mitigated throughout the organization. In the current economic climate this assurance and insight must be obtained with a high degree of efficiency, and new IT developments are increasingly used to achieve this. Implementing Continuous Auditing or Continuous Monitoring (CA/CM) not only contributes to obtaining efficient assurance and insight, but often also provides insight into potential ways to establish reliable and efficient business processes.
The added value that CA/CM provide for organizations
In general, CA/CM adds value by improving compliance with laws and regulations and by supporting business goals. From a technology perspective, CA/CM enables a high degree of automation for monitoring systems and data, and implements closed-loop mechanisms for any exceptions detected. As a monitoring mechanism, CA/CM helps to detect irregularities in system configurations, processes and data, either from a risk or a performance perspective. Potential benefits of CA/CM include:
- Enhanced and more timely oversight of compliance across the enterprise;
- Improved efficiency and effectiveness of the control environment through automation, leading to cost-reduction opportunities;
- Business improvement through reduced errors and improved error remediation, allowing reallocation of resources to activities that add value;
- The ability to report more comprehensively on compliance with internal and regulatory requirements
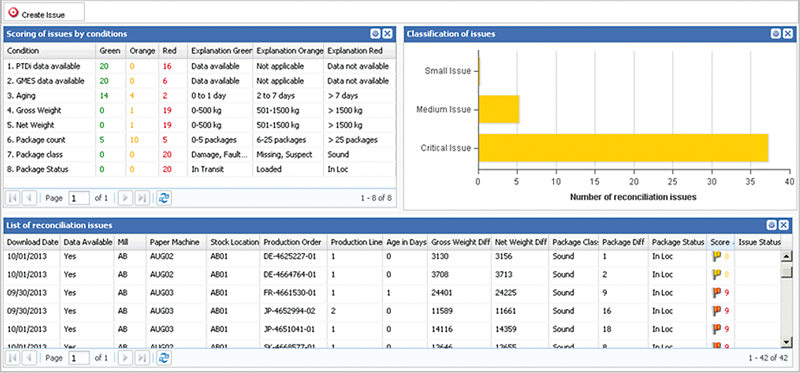
Figure 1. Sample compliance monitoring dashboard for IT. Source: BWise IT GRC solution.
The definition of CA and CM[[KPMG2008]]
Continuous auditing (CA) is the collection of audit data and indicators by either the external auditor or the internal auditor in information technology (IT) systems, processes, transactions and controls on a frequent or continuous basis throughout a period of time.
Continuous monitoring (CM) is a feedback mechanism used by management to ensure that controls operate as designed and that transactions are processed as described. This monitoring method is the responsibility of management, and forms an important component of the internal control structure.
Main outcomes of the CA/CM survey
CA/CM is winning ground within organizations that aim for continuous control and continuous performance. The level of awareness, the increasing availability of tools and the aim for greater efficiency in assurance are important drivers for further investigation into what CA/CM can bring to the organization.
Examples of CA/CM tools
- BWise Continuous Monitoring & Audit Analytics
- SAP Fraud Management
- RSA Archer
- Aptean Event Management Framework
- IDEA Caseware Monitor
- Data2Act
- ACL AuditExchange
- Oversight Systems
- SecurityWeaver
This section summarizes the outcome of an online EMA survey. The online survey was rolled out across the EMA region and contains responses from 718 individuals. The respondents are primarily from internal audit departments as well as from boards of directors, operational/line management in the office of the CFO, and finance and risk management sectors throughout the organization.
Respondents do understand the benefits of CA and CM. As depicted in Figures 2 and 3, 89% of the respondents realize that CA aims to bring comprehensive assurance with greater coverage across the organization; and 90% understand that CM enables the detection and correction of irregularities and helps to identify process improvements. However, understanding the benefits of CA/CM alone cannot drive it forward. Strategic drivers include the pressure to strengthen governance, enhance performance and accountability and improve oversight for global operations. Operational drivers include the occurrence or risk of fraud and misconduct and process improvement through the identification of irregularities on a continuous basis. External drivers include the expanding regulatory and risk environment, scrutiny from rating agencies, and an uncertain economic environment.
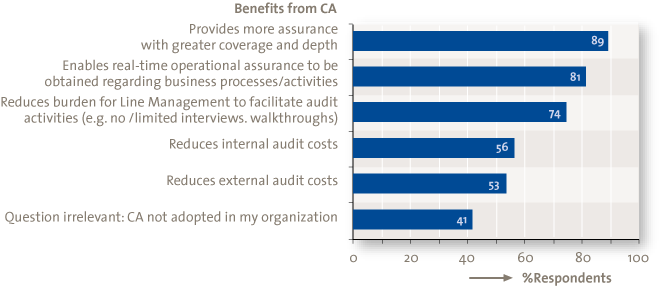
Figure 2. Benefits from CA.
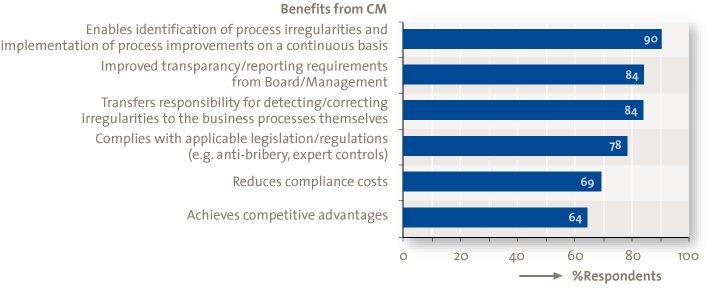
Figure 3. Benefits from CM.
CA/CM is considered to be most valuable in scenarios where processes are repetitive and susceptible to risk, e.g., financial management reporting (82%). These processes are often transaction-based and supported by applications with structured data. On the whole, CA/CM helps to foster a culture focused on efficiency. For example, organizations can use CM to help align components of the purchase-to-pay cycle so vendors are not paid too early but in line with the terms of the contract. Automating manual processes to detect issues early can save remediation costs. Obviously, preventing errors from occurring improves the overall business process efficiency as well.
Eighty five percent of the respondents stated that the internal auditors introduced CA/CM into the organization and that they are also seen as its main beneficiary (85%). Operational/line management is not often the initiator (59%) of CA/CM but certainly enjoys its benefits (85%). Internal audit often triggers CA/CM initiatives because it has experience with data analytics from a control testing perspective and CA constitutes the next logical step. Operational/line management is not often the first initiator of CA/CM but does benefit from it. This may be due to the fact that operational/line management does not solely act from a risk perspective – it is primarily responsible for the organization’s core business processes. However, operational/line management realizes that its responsibilities extend further and include internal controls, which are often closely linked to CA/CM.
The current state of adoption is low. Only 9% of respondents have both CA and CM embedded across their organizations. However, a remarkable 83% have at least considered implementing CA/CM. The main reason for this gap is that organizations find it difficult to quantify the benefits of CA/CM to justify the business case for its implementation. The first step towards adoption is to build a business case to secure support from senior management and to outline the objectives, scope, expected costs and projected benefits of CA/CM. Starting on a small scale (e.g., by experimenting with tools on pilot projects) allows management or internal auditors to test the CA/CM concept first. The next step is to draw up a road map to be able to fully achieve the objectives of the CA/CM implementation.
Respondents consider the limited insight into the CA/CM tooling available on the market as the largest barrier to the adoption of CA/CM (69%). As illustrated in Figure 4, it is not always clear what suitable CA/CM tooling should consist of. From our perspective, CA/CM tooling includes at least: data extraction (from source systems), data analysis, case management (to make exceptions actionable) and reporting (e.g., via dashboards). Advances in technology have paved the way for increased use of CA and CM in organizational processes, transactions, systems, and controls.
The success of a CA/CM initiative is highly dependent upon the effective implementation and use of the right technology tools. In the same way, those tools will only be successful if used effectively. Currently 75% of the respondents are using IT tools, with only 13% of them using business intelligence (BI) dashboards and 10% using dedicated CA/CM tools. Furthermore, CA/CM is partly a technology solution and this obviously requires expert knowledge.
Organizations need to evaluate how suitable the features, functions and capabilities of any tool are for their needs before engaging a specific tool provider. They should take steps to increase their knowledge and become more familiar with the concepts of CA/CM in order to overcome specific barriers to the implementation of CA/CM.
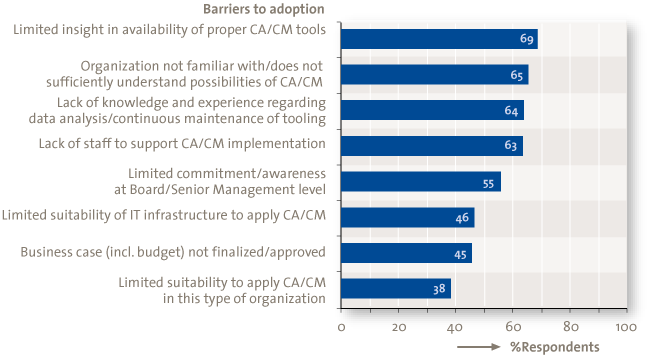
Figure 4. Barriers to adoption.
Organizations are changing from just being interested in CA/CM to actually investing in CA/CM-related projects. In the next two years, the percentage of organizations that are not investing in CA/CM will decline from 37% to 19%, while 62% expect to commence projects valued at up to €250,000 (Figure 5). Organizations are eager to learn, but shy away from high up-front investments. Some companies have successfully managed the cost challenges associated with CA/CM by integrating these into wider project budgets. For companies looking to implement CA/CM, pilots can deliver results quickly and potentially help CA/CM to become auto-financing. An investment in CA/CM fits well in the context of a larger business intelligence initiative where CA/CM can provide critical business decision-making capabilities. In most other cases, an incremental approach based on an ROI analysis may be more appropriate.
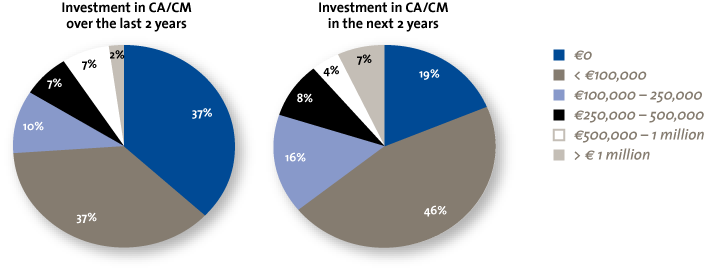
Figure 5. Past and future investments in CA/CM.
The key observations of the EMA survey are:
- Respondents do understand the benefits of CA and CM. They realize that CA aims to bring comprehensive assurance with greater coverage across the organization. Many believe CM is set up to detect and correct process irregularities and helps to identify process improvements;
- CA/CM is considered to be most valuable in scenarios where processes are repetitive and susceptible to risk, e.g., financial management reporting;
- Most of the respondents stated that the internal auditors introduced CA/CM into the organization and that they are also seen as its main beneficiary. Operational/line management is not often the initiator of CA/CM but certainly enjoys its benefits;
- The current state of adoption is low. However, a remarkable number of respondents have at least considered implementing CA/CM;
- Respondents consider the limited insight into the CA/CM tooling available on the market as the largest barrier to the adoption of CA/CM. It is not always clear what suitable CA/CM tooling should consist of;
- Organizations are changing from just being interested in CA/CM to actually investing in CA/CM-related projects.
Case study: large-scale implementation of CA/CM
Background
The client was accused of paying bribes. This accusation led to comprehensive investigations by the government. The bribes were paid to secure new deals. An estimated total of 14 million euros in bribes was paid in the period between 2002 and 2005. As result of the investigations, the client had to pay a fine of 150 million euros for failing to follow government regulations. In addition to the fines, the client received a lot of negative publicity and a number of board members and employees were terminated.
Design and build phase
The public prosecutor said that there was no sufficiently effective internal control system for detecting bribes. Therefore, a solution to monitor the entire purchase-to-pay process had to be introduced. The design phase resulted in 23 blueprint documents regarding system architecture, data analytics, security, training, etc. In the design phase a lot of attention was paid to the flexibility and scalability of the solution, in order to make the solution applicable for future extensions such as order-to-cash controls, IT controls and business performance indicators.
Due to very specific client requirements, the solution existed of a combination of software applications and databases (Figure 6) instead a of commercial off-the-shelf CM software. Key requirements were connection to multiple source systems, both SAP and non-SAP and integration with Microsoft SharePoint for case management and reporting. The scheduling tool was used to trigger the data extraction and data analytics processes in the backend. The data analytics rules (queries) were build in an Oracle database (the standard database at this client). The results of the data analytics were pulled into a Microsoft SQL Server database to allow integration with Microsoft SharePoint.
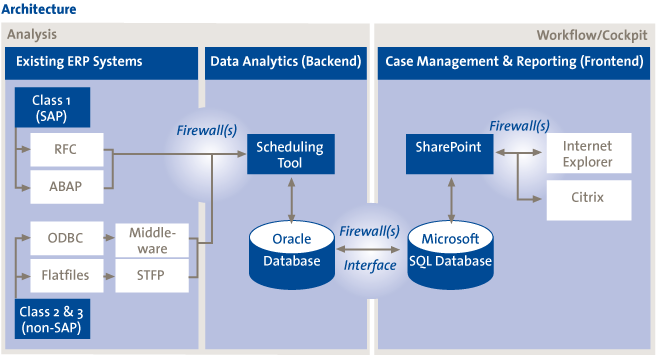
Figure 6. Conceptual overview of CM architecture
To monitor the entire purchase-to-pay process 40 controls were defined in two categories: process controls and access controls. The process controls consisted of master data controls (e.g., changes to bank accounts), transactional controls (e.g., direct invoices), customizing controls (e.g., changes to three-way-match settings) and transactional analysis to detect violations in the segregation of duties (e.g., posting of an invoice and purchase order by the same person). The access controls consisted of personnel authorizations (e.g., who is authorized to process payment) and segregation of duties (e.g., who is authorized for both posting purchase orders and invoices). Figure 7 depicts an overview of the main controls in the different sub-processes of the purchase-to-pay process. As described in the previous section, we think that for companies looking to implement CA/CM, pilot projects can deliver results quickly and potentially help CA/CM to become auto-financing. As an example, organizations can start a pilot project with only one source system and select the most critical controls of the purchase-to-pay process to implement.
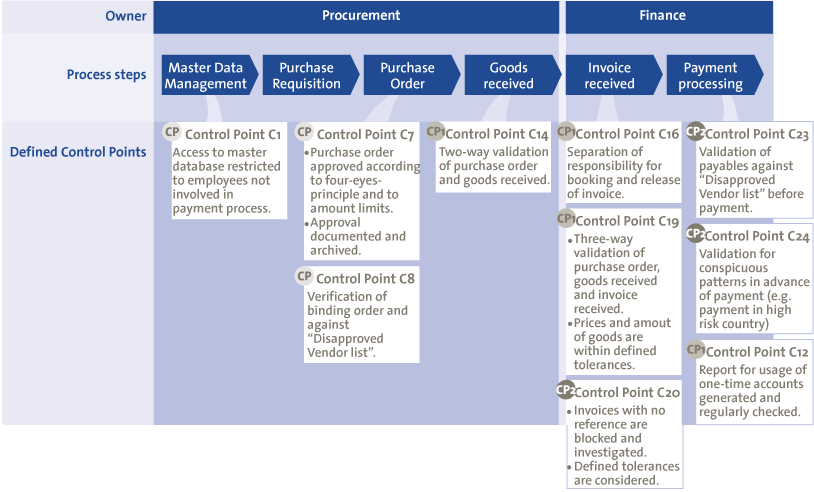
Figure 7. Overview of controls in the purchase-to-pay process.
During the development phase significant effort was put into building workflows to provide follow-up when alerts were triggered, to escalate the level of alert in some cases, and to reduce false alarms. For some alerts a dynamic workflow was used: the person who triggered an alert in the source system (e.g., SAP) was also the person who received the alert. This led to a reduction in workload: i.e., the person who could best explain and solve the alert was directly involved in the follow-up.
For each alert a second person (often the boss of the first person) would be informed about the alert, as part of ensuring disclosure of alerts. This person was also responsible for reviewing the explanation and possible remedial action by the first person. In addition, an escalation workflow was triggered in case no timely follow-up was performed. Escalation included multiple steps with particular time intervals (e.g., 30 days). The last escalation step was informing the CFO.
In case an alert was a false alarm, an exception or override could be created. An exception could be based on information identified by the alert-triggering mechanism indicating that an alert is unnecessary. The fields in the alert on which the exception could be created were predefined (e.g., vendor) and the content of the field could not be changed: e.g., if an alert contained information about vendor ABC, no exception could be created for vendor XYZ. The creation of each exception triggered a new workflow for approval because it was a critical function (future alerts were excluded). Each year internal audit reviewed all exceptions, to ensure that only appropriate exceptions were created.
Roll-out phase
After the implementation of the CM solution the next step was to do a roll-out of the solution to the different sites and countries including Germany, France, Switzerland, Denmark, US, China. Two implementation teams were created (one for each division) that travelled to the countries where the client had local sites. A typical roll-out included the following phases: preparation, delta concept, configuration, test & acceptance and go-live. The preparation phase included the explanation of the CM solution, the controls and the roll-out process to the local site.
The purpose of the delta concept, which consisted of a number of workshops with the purchasing and finance department, was to verify whether the controls in the CM solution were applicable for the local site (e.g., a control might not be applicable because the local business process was different). Based on the delta concept it was decided which controls could be implemented for the local site and which exceptions could already be configured (e.g., exclusion of specific general-ledger accounts). Secondly, a dry run was performed on the controls with actual data from the site. The alerts created based on the dry run were reviewed with the business, and settings were adjusted in the CM solution to remove false positives that would trigger false alarms.
In the test & acceptance phase the user acceptance test was performed. People from the purchasing and finance department had to post bookings in the source systems. We knew that some would lead to alerts and some not. These people were then asked to check the CM solution to see whether an alert had been created or not. Furthermore, in this phase the people were also trained in using the CM solution.
The final phase of the roll-out was the Go-live. When the CM solution produced stable results (i.e., an appropriate number of alerts) for a couple of weeks in a row, a decision was made to perform a complete go-live or to do a partial go-live (a limited set of controls).
Results and critical success factors
The implementation of the CM solution was a success: a lot of irregularities were detected via the CM solution, although most were related to human errors instead of fraud. After some initial skepticism at the local sites, people starting seeing the advantages of such a powerful tool. It reduced manual work in monitoring controls and it detected human errors. As result of positive feedback, plans are now being made to expand the usage of the CM solution to more areas than controls alone: for example, to improve business performance. The critical success factors of this project were:
- Building a CM solution of standard technology components already in use by the client
- The buy-in of the client’s key stakeholders and project members
- A flexible and scalable solution regarding growth, functionality and multi usage
- A lot of attention on end-user acceptance (e.g., through reducing false alarms)
In the next part we will describe lessons learned based on this and other CA/CM implementations.
Implementing CA/CM: The lessons learned
Organizations should realize that effective implementation of CA/CM can take time and effort. A variety of challenges can be expected along the way. Implementing CA/CM goes beyond technology. It is about changing the nature, speed and visibility of information on risk and performance. This should ultimately transform the way in which business decisions are being made and monitored. But most of all, implementing CA/CM is about understanding the extent to which CA/CM can transform processes, risk and controls, technology, and people.
Lessons have been learned from CA/CM implementations at different organizations:

Figure 8. Lessons learned for achieving successful CA/CM implementations.
1 Start with smaller pilot projects to explore the potential of the CA/CM concept
For companies looking to implement CA/CM, pilot projects can deliver results quickly and potentially help CA/CM to become self-financing. An investment in CA/CM fits in well in the context of a larger business intelligence initiative where CA/CM can provide critical business decision-making capabilities. In most other cases, an incremental approach based on an ROI analysis may be more appropriate.
To enhance the impact of the pilot project it is critical to only select controls or KPI’s for CA/CM that directly result in significant reduction of critical risks or in business performance improvements. After a successful pilot the actual CA/CM implementation can include more controls and KPI’s to have wider coverage of risks and potential performance improvements.
2 Manage cost challenges by integrating CA/CM pilots into wider projects
One way that some companies are getting round the issue of cost is to build CA/CM into wider projects, such as major ERP or GRC implementations or upgrade projects. Typically these projects have significant budgets and expenditure on CA/CM is small in comparison. This moves the cost burden away from cost centers (like internal audit) that have very little spare budget. It can also expand the potential value, by recognizing the benefits of business process efficiency and by ensuring that control and compliance efforts of different compliance functions are coordinated, using the same methods and tools ([KPMG2010]).
3 CA/CM is largely just automating manual labor, which can be used as a business case
During the current economic downturn, budgets are tight and competition for funding is tough. The first step towards adoption is to build a business case to secure support from senior management and to outline the objectives, scope, expected costs and projected benefits of CA/CM. Automating manual processes to detect issues early, prevent escalation of problems and decrease the manual analysis or intervention needed can save retrospective remediation costs. Obviously, preventing errors from occurring improves the overall business process efficiency as well. Typically, areas that tend to have the greatest return on investment (ROI) in an initial CA/CM implementation include manual journal entries, time and expense, tax, purchase-to-pay, order-to-cash, and inventory management.
4 Get involvement from business owners, compliance regulators, and assurance providers directly from the start of the project
We have found that internal audit is often the catalyst to get CA up and running, and that CA can be implemented successfully without CM. But, in the long run, management typically ends up adopting some of those responsibilities commonly associated with CM, thus allowing audit to provide assurance over the effectiveness of management’s CM processes and helping prevent the lines of responsibility from becoming blurred.
5 Investigate whether you can leverage software you have already purchased
CA/CM is partly a technology solution, so it obviously requires expert knowledge. At the same time there appears to be uncertainty about what functionality CA/CM tooling actually provides. From our perspective, CA/CM functionality includes at least data extraction (from source systems), data analysis, case management (to make exceptions actionable) and reporting (e.g., via dashboards). Organizations often have “in-house” tooling which includes one of these functionalities. If this is the case, then investigating whether they can leverage this software may be a more appropriate alternative than implementing expensive CA/CM tools.
6 Integrate CA/CM as much as possible in the existing management reporting structures
Typically, CA/CM is most valuable in scenarios where processes are repetitive and susceptible to risk (e.g., financial management reporting). These processes are often transaction-based and supported by applications that run on structured data. CA/CM tooling implemented on applications that run on structured data can easily be modified and extended to meet specific management reporting requirements.
7 The number of false alarms should be at an acceptable level to ensure buy-in from the end-user
Before significant resources are allocated to monitoring controls and transactions, management will need to consider whether the existing controls are the most effective to be able to address the underlying risks. In addition, management should give careful consideration to what should be measured, where the necessary data resides, and the quality of the data. Simply “switching on” rules that may exist within a standard technology tool without refining them could result in an unmanageable number of “exceptions” or “false positives” requiring attention, in turn resulting in increased inefficiencies as well as a false sense of assurance. Similarly, “switching on” poorly designed rules may also result in a false sense of assurance.
8 Visualizations can help the business to identify trends and improvement opportunities
CA/CM gives managers and auditors greater visibility into processes, activities, and transactions. However, visualizing the information in dashboard form gives business greater visibility into processes, activities, and transactions. In addition, visualized information can generate other specific benefits for the enterprise: e.g., identifying trends and improvement opportunities.
Figure 9. Example CA/CM dashboard for accounts receivable including trends (Source: BWise CM).
9 Organizational change and moving towards an information-driven culture is key
Organizations should understand that CA/CM is not only about implementing tooling; it is a change in the way of working where you have to redefine your objectives, roles and responsibilities and the way to handle the “informative” outcome. Moreover, implementing CA/CM is about understanding the extent to which CA/CM can transform processes, risk and controls, technology, and people in an integrated way. When implementing CA/CM, organizations typically follow several stages of maturity, starting with the introduction of data analytics techniques to support existing manual procedures. Depending on the drivers behind CA/CM, the end state may be CA/CM systems that are fully embedded and used throughout organizations.
Role of external auditor/advisor regarding CA/CM
As elaborated in the previous section, management and internal audit understand controls, but there is often a lack of understanding regarding the concept of CA/CM and its benefits. They may not be aware of the emerging field of CA/CM software. Therefore there is an opportunity for external auditors and advisors, who bring a broader focus on improving the business and who recognize CA/CM as low-hanging fruit, to recommend specific CA/CM solutions that can impact the business in a positive way. The external auditor/advisor with knowledge and experience in data analytics, control monitoring, KPI’s and reporting dashboards can help clients to point out these benefits and explain how CA/CM could be applied in their organization.
Besides that, external auditors/advisors can play an important role before, during and after the implementation of CA/CM. They can use their expertise and industry knowledge to help organizations with CA/CM in different ways:
- Building a business case for CA/CM including effects on ROI;
- Designing a CA/CM framework that supports strategic management objectives;
- Assist in designing and implementing CA/CM (e.g., creating dashboards, scorecards, analytics, and management protocols);
- Optimizing controls and performing root-cause analyses for control failures;
- Evaluating the CA/CM methodology and/or project; and
- Providing training on CA/CM and the usage of CA/CM tooling.
Conclusion
The survey showed that there is a high degree of awareness of the potential benefits of CA and CM to organizations. Despite the interest to-date, only a limited number of organizations have been involved in an enterprise-wide adoption of CA/CM practices, largely due to the lack of a suitable business case or their inability to effectively measure the benefits of such initiatives. However, with the growing interest in risk assessment and compliance monitoring, there are strong prospects for CA/CM practices to be adopted by more businesses in the foreseeable future.
The survey further revealed that the functions across an organization gained added value from CA/CM practices, irrespective of whether they were the initiators. Beyond other functions, internal audit remains the main initiator and beneficiary of CA/CM. Other services, such as operational/line management, are not usually the first initiators of CA/CM, but benefit from it.
Most respondents believe that CA/CM is best suited to support processes such as “financial management reporting,” regulatory reporting and “treasury and cash management.” Typically, the areas that tend to have the greatest return on investment (ROI) included “manual journal entries,” “time and expense,” “purchase-to-pay,” “p-cards,” “order-to-cash” and “inventory management.”
Our recommendation is that to fully benefit from each CA/CM initiative, management should focus on achieving a healthy ROI, while focusing on lowering exposure to risks. Pilot projects, with a limited set of analysis and connections, may deliver results quickly and potentially help CA/CM to become self-financing, thus fuelling the business case for adopting an enterprise-wide CA/CM program.
Finally, we believe that organizations that are interested in CA/CM need guidance and sufficient information on the benefits and techniques associated with CA/CM. Here’s where external auditors and advisors come into play. The success of a CA/CM initiative largely depends on its effective implementation and integration in day-to-day operations, as well as the judicious, appropriate and effective use of technology.
Organizations should realize that effective implementation of CA/CM can take time and effort. A variety of challenges can be expected along the way. No matter how they choose to launch the effort, organizations should look to define the desired end-state for their CA/CM efforts. Organizations should understand that CA/CM is not only about implementing tooling, it is a change in the way of working where you have to redefine your objectives, roles and responsibilities and the way to handle the outcome. Moreover, implementing CA/CM is about understanding the extent to which CA/CM can transform processes, risk and controls, technology, and people in an integrated way.
Based on our practical experience in supporting organizations before, during and after the implementation of CA/CM initiatives, we strongly believe that this will be a way forward to create greater transparency in an efficient and sustainable way. With the evolution of CA/CM we predict an organizational shift regarding the providers of assurance and analysis: from internal audit and risk management (3rd and 2nd line of defence) towards management (1st line of defence), as illustrated in Figure 10.
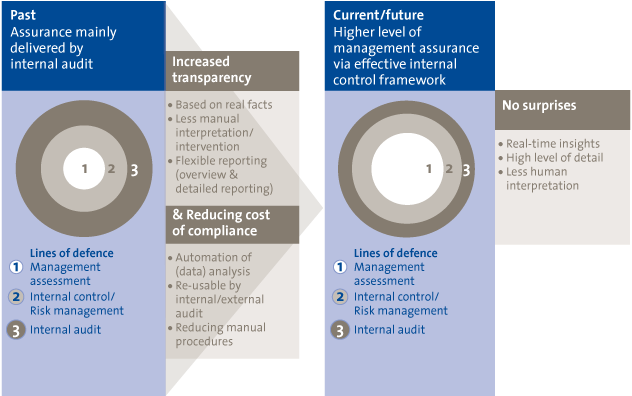
Figure 10. Organizational shift regarding the providers of assurance and analysis.
References
[KPMG2008] KPMG, “Continuous Auditing and Continuous Monitoring: Transforming Internal Audit and Management Monitoring to Create Value,” 2008.
[KPMG2010] KPMG, “Continuous Auditing and Monitoring: Are Promised Benefits Now Being Realized,” 2010.





